

Once the IACS infrastructure and data flows are understood, you can develop risk profiles for each zone and allocate a criticality or security level to the zone defined by the potential consequence arising from compromise of the assets or functions of that zone.
Similar to a process safety risk assessment, a cyber security risk assessment should define the potential worst-case outcome for each zone relative to the organisation’s regulatory framework e.g. COMAH, or to a corporate risk matrix (for companies not operating under a legal duty to implement OT cyber security practices). OG86 requires that Major Accident (safety, health, and environmental) and Loss of Essential Services consequences are examined, for organisations falling under the HSE’s authority, however, companies operating under different or no regulatory framework may wish to include other risk metrics e.g. business continuity, profitability or reputation.
Risk assessments will require input from a broad range of competencies, typically:
IACS responsible persons (Duty Holder in Major Accident workplaces),
It is also important to include representation from other business functions which can impact the cyber security and resilience of chosen IACS and security systems e.g. Procurement, Human Resources and Legal Departments.
There are many methodologies for conducting cyber security risk assessments, e.g. the ISO 62443-3-2 high-level cyber security risk assessment which is taken as the basis of the OG86 Appendix 4 risk assessment example. Unlike process safety risk assessments, a cyber security high level risk assessment assumes a threat likelihood of one (certain to occur) and focuses on evaluating the worst-case outcome of an IACS zone or asset being compromised to determine the areas of highest risk.
The risk assessment scenarios need to be realistic and feasible so should be based on up-to-date vulnerability information and threat intelligence relevant to the IACS hardware, software and architecture defined in the organisation’s simple network diagram and IACS asset register and must be initially assessed without taking credit for any existing cyber security countermeasures.
A high level cyber security risk assessment methodology is summarised in the flow chart below:
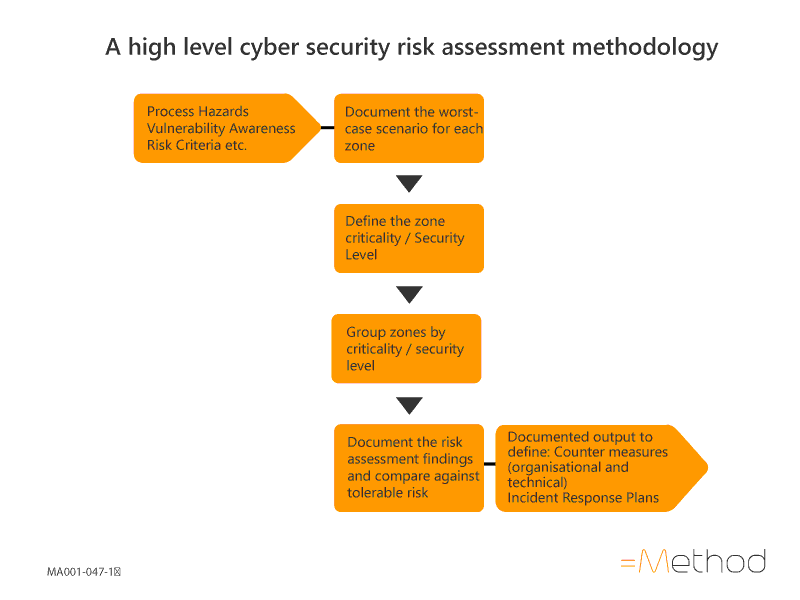
Where the high level risk assessment identifies risks which exceed the organisation’s tolerable risk criteria, further detailed cyber security risk assessments should be performed to identify additional countermeasure necessary to reduce the risk.
A key countermeasure is the secure design and segmentation of the zones and conduits.
You can contact =Method below:
p: +44 (0)1462 713313
E: support@methodcysec.com. T: 44 (0)1462 713313. W: www.methodcysec.com