

To defend a system you first need to understand its components and interactions. The scope of the control system(s) requires to be comprehensively defined and recorded to enable accurate risk assessment and ongoing management of cyber security.
It is recommended that the control system is recorded as a simple network diagram and associated asset management data (IACSIndustrial Automation and Control Systems asset register). As cyber security risk management is an ongoing iterative process, updating the simple network diagram and IACS asset register is a continuous process which should for part of the organisation’s Change Management process.
The boundary of an IACS / OTOperational Technology system must include all physical and logical (i.e. network interfaces, trust relationships and data flows) digital technology assets involved in process control and safety actions and should be physically and logically segregated from non-IACS networks e.g. Corporate Local Area Network (LAN) or internet-facing networks.
The IACS scope can be recorded using a system-by-system (bottom up) or system-of-systems (top down) analysis approach. For organisations beginning their cyber security journey, the bottom up approach, starting with critical process control and safety systems, would be recommended.
The following (suggested but not exhaustive) list of assets to be included in the IACS scope is an excerpt from OG86 (Edition 2):
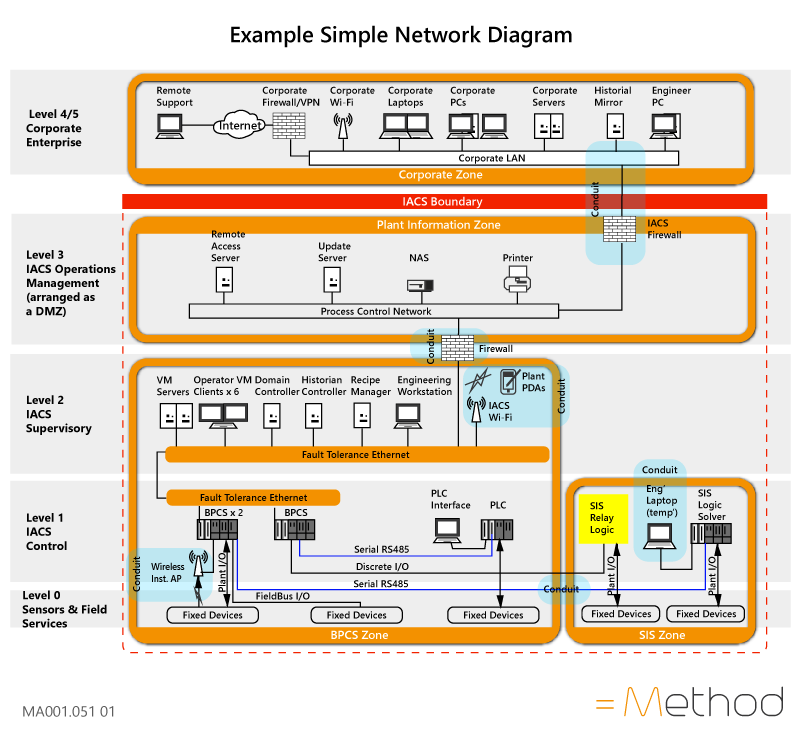 Diagram 2. Example of a Simple Network Diagram for a medium-sized organisation (from HSE OG86)
Diagram 2. Example of a Simple Network Diagram for a medium-sized organisation (from HSE OG86)
You can contact =Method below:
p: +44 (0)1462 713313
E: support@methodcysec.com. T: 44 (0)1462 713313. W: www.methodcysec.com